The API Security Imperative: Protecting Your Enterprise in a Hyperconnected World
APIs are the backbone of modern-day interconnected businesses, enabling seamless integration and communication with partners and customers. However, their increasing importance has made them a prime target for cybercriminals. Shockingly, Gartner predicts that API abuses will become the most frequent attack vector this year, leading to data breaches in enterprise web applications. Moreover, unsecured APIs are expected to cause over 50% of data theft by 2025. It’s time for your business to take control and adopt the best practices of API security.
Deciphering OWASP’s Top 10 API Security Threats
OWASP’s prioritised and actionable Top Ten lists offer invaluable guidance on the most critical security risks for enterprises. Specifically, it addresses vulnerabilities in APIs, helping organisations identify and mitigate potential threats. The security threat of each API is evaluated based on exploitability, weakness prevalence, weakness detectability and technical impact. This enables organisations to prioritise vulnerabilities according to severity, allowing for a more focused and effective approach to API security.
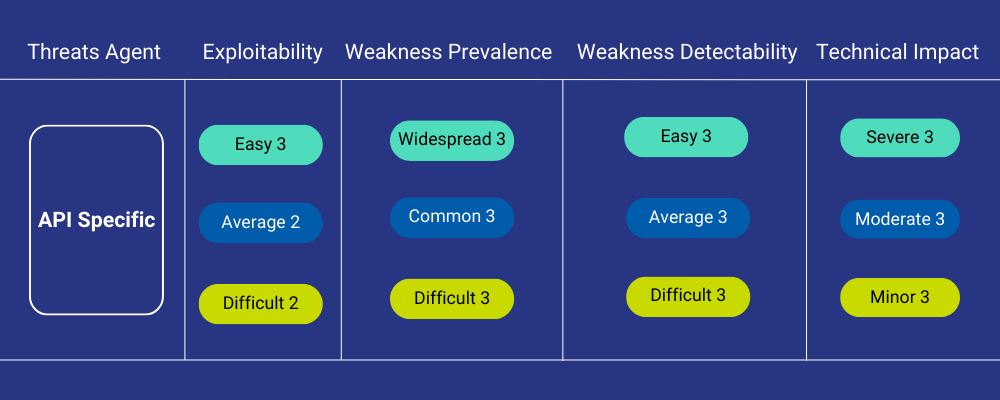
Unveiling the OWASP Top 10 API Security Threats in Open API Systems
In a world of open API systems, the following OWASP Top 10 API security threats warrant your attention:
API1 – Broken Object-Level Authorisation

APIs that have endpoints handling object identifiers pose a massive attack surface in access control. To prevent unauthorised data manipulation, individual authorisation checks are critical. This cheat sheet offers developers a secure permission logic and an approach for automating authorisation matrix tests.
API2 – Broken User Authentication

APIs have a more complex authentication process than web applications as human-driven options like MFA are not viable. Incorrect implementation of authentication mechanisms can lead to compromised tokens or exploited flaws, enabling attackers to take over user identities and weaken overall API security. This cheat sheet provides guidance on user IDs, authentication solutions, password strength, recovery controls, protection against automated attacks, and authentication protocols like MFA and CAPTCHA.
API3 – Excessive Data Exposure

To enhance functionality, developers may inadvertently expose all object properties in APIs, regardless of their sensitivity. This relies on clients to filter the data before presenting it to users, potentially causing excessive data exposure.
API4 – Lack of Resource & Rate Limiting

APIs often lack restrictions on resource size or request frequency, enabling users to make excessive requests, either accidentally or intentionally. This can degrade server performance, potentially leading to Denial of Service (DoS) attacks and exposing authentication vulnerabilities like brute force attacks. This cheat sheet offers insights into DoS attacks and guidelines for handling various scenarios, encompassing both application and network attacks.
API5 – Broken Function-Level Authorisation

Flaws often arise in intricate authorisation policies with hierarchies, roles and groups, and blurred distinctions between admin and regular functions. Attackers can exploit these vulnerabilities to access other users’ resources or administrative functions.
API6 – Mass Assignment

Attackers can exploit object properties by predicting them, examining API endpoints, perusing documentation, or appending extra properties in request payloads. Inadequate filtering of client-provided data (e.g., JSON) based on an allowlist, when bound to data models, often leads to Mass Assignment.
API7 – Security Misconfiguration

Small errors during set-up can lead to security misconfigurations, such as open cloud storage, insecure defaults, incomplete configurations, misconfigured HTTP headers, unnecessary HTTP methods, permissive Cross-Origin resource sharing and/or verbose error messages containing sensitive information. This cheat sheet focuses on using Transport Layer Security (TLS) to protect clients connecting to a web application over HTTPS, with most guidance applicable to other TLS uses. HTTP Strict Transport Security is an opt-in enhancement specified via a response header, which enforces communication over HTTPS and prevents click-through prompts on browsers; learn more in this cheat sheet.
API8 – Injection

Failing to separate data and code can lead to issues. Untrusted data sent to an interpreter as a query or command may result in injection flaws like SQL, NoSQL and Command Injection. Attackers can manipulate data to deceive interpreters into executing unintended commands or accessing data without permission. This cheat sheet offers concise guidance to help avoid injection flaws in applications.
API9 – Improper Asset Management

Protecting your assets requires awareness of their existence. Thorough API inventory and documentation are vital, as APIs present more endpoints than conventional web applications.
API10 – Inadequate Logging and Monitoring

APIs are not inherently designed for robust integration with top-level security tools. Ineffective logging and monitoring, paired with insufficient incident response, can enable hackers to attack systems, maintain persistence and access other systems to manipulate or destroy data. Breaches often go undetected for over 200 days and are typically discovered by external parties. This cheat sheet offers guidance on developing secure application logging mechanisms.
Top 10 Strategies for CISOs
As a CISO, the responsibility of securing your organisation’s sensitive data and preventing attacks on APIs falls on your shoulders. But fear not, as we have curated a list of best practices inspired by the OWASP Cheat Sheet Series to help you fortify your organisation’s API security against the Top 10 threats:
- Robust Authentication and Authorisation: Embrace state-of-the-art authentication and authorisation mechanisms, such as OAuth 2.0 and OpenID Connect, to thwart unauthorised access to your APIs.
- Rigorous Input Validation: Ensure meticulous validation and sanitisation of all incoming data to forestall injection attacks, including SQL injections and cross-site scripting.
- Secure Data Transmission: Utilise encrypted communication channels, such as HTTPS and TLS, to safeguard sensitive data in transit.
- Employ Rate Limiting and Throttling: Shield your APIs against DoS attacks by constraining the number of requests per user within a specific timeframe.
- Comprehensive API Activity Auditing and Monitoring: Regularly scrutinise and monitor API usage to detect anomalous activity and potential security threats.
- Impenetrable API Deployment: Implement fail-safe API gateway configurations and leverage secure API management platforms to prevent misconfigurations that could expose your APIs to attacks.
- Consistent Error Handling and Logging: Establish uniform error handling and logging protocols to prevent information leaks and expedite incident response.
- Diligent Updates and Patching: Continuously update your APIs, dependencies and underlying infrastructure with the latest security patches to deter the exploitation of known vulnerabilities.
- Adherence to Security by Design Principles: Integrate security throughout the API development lifecycle, ensuring that security best practices are diligently followed during design, development and deployment.
- Fostering a Security-Centric Culture: Equip your development team with comprehensive API security knowledge, fostering a culture of security-conscious development.
In addition to the above, building a robust API security structure requires three key capabilities: API Posture Management, API Runtime Security and API Security Testing.
Beyond OWASP: Building Robust API Security
In today’s app-driven world, building a robust API security structure is a necessity. To protect your enterprise from the rising threat of API vulnerabilities and attacks, posture management, runtime security and API testing are key capabilities that must be leveraged. And when it comes to identifying and mitigating potential threats, the OWASP API Security Top 10 provides an excellent starting point. But why stop there? Download our partner eBook for in-depth details on how to build a robust API security structure that can discover APIs before attackers do, analyse API behaviour and remediate any source of API risk.
Don’t wait for an attack to happen, act now and safeguard your enterprise’s sensitive data; contact us if you want to discuss how to obtain a secure API platform.

